In simple words, VoIP is not entirely safe from hackers.
Even though there may be difficulties in protecting your company against VoIP hacking, with the knowledge of some warning indicators and some effective action plans; one would still know that his business is protected.
Therefore, learning the signs that some malicious actions are about to happen to your VoIP Network and taking the required steps to prevent them forms the keystone in protecting your VoIP Network and other business operations.
Also, it is imperative to consider the question whether VoIP can be treated as safe from hackers. In what ways, is VoIP vulnerable? VoIP is quite cost-effective and improves communication, but security can be a concern.
Attacks such as VoIP hacking, toll fraud, phishing attacks, and DoS may involve hackers using weaknesses in VoIP to achieve their objectives. Because of this, companies have to be on their toes with good security measures to lessen such risks.
Businesses may minimize the risk of being attacked by staying alert to possible VoIP security dangers, checking for anomaly behavior and abuse and employing a wide array of security measures.
Furthermore, facilitating efforts for potential undesired actions would also be possible due to cooperating with any of the trusted providers of VoIP services who pay special attention to safety.
Nevertheless, it is important to know that, like any other technology, there is a downside to VoIP. This downside is what can be termed as a weakness because it is more vulnerable to the nefarious practice of e-crimes, hacking and tapping into the VoIP system.
It is the aim of this paper to examine the dangers involved in VoIP hacking, tapping focus, and the risk management framework to help avert such a danger.
What is VoIP Hacking?
Voice over Internet Protocol hacking is regarded as a special type of hacking since the perpetrators focus solely on the VoIP system and use the internet connection to get into the user’s phone systems.
This breach can go through your entire network, giving them the ability to eavesdrop on calls, not only place unauthorized orders, send fraudulent messages using the authority of executives but also take away crucial information pertaining to you and your client.
Inherent vulnerabilities of VoIP systems prompted hackers to penetrate into the systems for different reasons including access to critical data, communication monopolization, hindering of services, and sneaky actions like fraudulence.
Such actions are unwarranted and include the guesswork of passwords, social engineering, eavesdropping, ddoS kind of attacks and viruses.
It must be noted that Voice over Internet Protocol VoIP hacking has its ramifications as it really affects the natural confidentiality, integrity and availability of the communication system both to a business entity and to individuals.
The repercussions of voIP hacking is serious in nature and poses threat to the confidentiality integrity, and availability of communication systems of many organizations and people as well.
Is VoIP Safe From Hackers?
To sum up, VoIP is still not safe from intruders. VoIP technology possesses many benefits when it comes to cost concern and features but at the same time, it delivers areas of weaknesses which attackers use.
One particular reason that accounts for a high rate of occurrence of VoIP attacks is that it relies on IP networks for transport of voice signals.
VOIP calls are dangerous because the phone calls can be hacked or snooped upon, which is why they present security challenges of their own including toll fraud, eavesdropping, call spoofing, and DoS attacks among others.
Besides, poor configurations, weak passwords and e-mail systems, and use of low-level security software can in additional worsen the efforts of protecting VoIP networks.
It stands to reason therefore that organizations need to further secure their VoIP infrastructure by adopting advanced technologies including encryption, network segregation, secured login protocols and frequent system upgrading to eliminate these vulnerabilities.
How Do VoIP Hacking Take Place?
Voice-over Internet Protocol hacking It is crucial to comprehend the different strategies employed by attackers in fortifying measures.
Any VoIP-System can be hacked using different methods and every one of those approaches is regarded as VoIP hacking.
Here’s how it works, along with real-time examples.
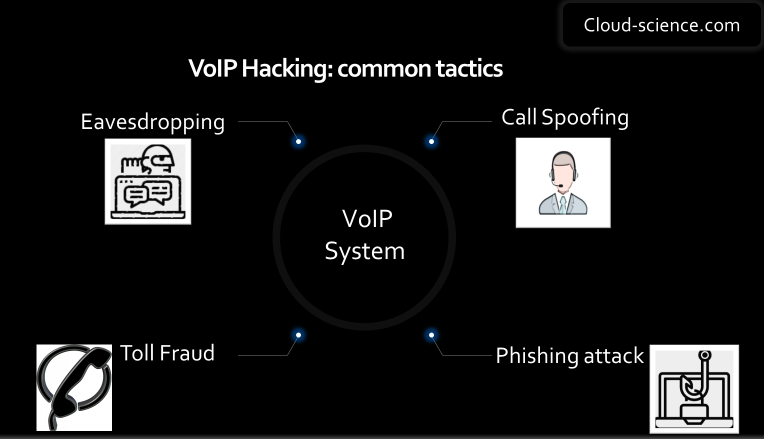
1. Eavesdropping:
Eavesdropping refers to listening in on peoples’ conversations without consent and obtaining private information from them e.g., passwords, financial information, trade secrets.
This is an unethical act which in one way or the other leads to the invasion of one’s security and privacy posing a threat such as theft of identity, misuse of finances, and in corporate situations corporate spying.
If you accept payments over the phone or you interfere with the customers asking for personal information, then combating against eavesdropping becomes an important issue here.
VoIP traffic may be compromised by VoIP packet sniffer network attacks due to poorly adapted network security services, and packet snoopers on unsecured Wi-Fi, that do not provide Transport Layer Security and Real-time Transport Protocol.
Such activities allow attacker’s room to surveil the system and steal information in the network.
Example: Eavesdropping
Imagine a small business using a VoIP system for customer calls in a real-world scenario. An attacker intercepts these calls over an insecure Wi-Fi network without proper security measures like encryption.
They eavesdrop on a call where a customer provides payment details, enabling the attacker to steal sensitive information for fraud.
2. Call Spoofing:
A VoIP service has features that allow call spoofing which involves forging the phone number of the person who calls.
It is easy for attackers to hide their identity under that of a trusted person or organization and then trick the users in a way that makes them give away confidential data, complete transactions that aren’t real or log onto facilities or installations that they are not authorized to access.
When a call comes through and a number or an ID is shared with the phone, do you trust the number or ID shared with the phone?
Trust is not always guaranteed whenever a person receives a phone call that has a number or a caller ID displayed. One of the trick that is used in this common case is called caller ID spoofing which tries to mask the true source of the call and trick someone in order for them to answer the call.
Example: Call Spoofing
In this case, a hacker could spoof a cell phone number to that of the bank. As a result, a targeted victim would provide their telephone details, such as their bank account number over the phone. Similarly, a hacker could make use of spoof techniques by making it look like the bank’s phone number is calling them.
They mimic the work of the bank and try to make the victim believe that it is a really and convincingly secure phone call. After that, the hacker can then get them to reveal some personal banking details, such as their account numbers and their passwords, over the phone.
3. Denial of Service (DoS) Attacks:
Denial of Service attacks target VoIP networks (IP telephony networks) to disrupt servers, networks, or endpoints making them unavailable to legitimate users. This results in the downgrading of communication efficiency which brings about loss, both time and funding, in the organization.
By abuse of excessive spanning towards the attacked system or via redundancy, some critical functions of the voice communication would be temporarily cut off.
Example: (DoS)
For instance, an undoing of a cascading falling effect might be realized. A person, even a stalker, can bombard a Voice over Internet Protocol server with multiple cellular call requests which would, in turn, lead to the working call VoIP services even to the users attempting to make proper calls, Conversations would temporarily be of poor quality or even be stopped entailing some VoIP hassles.
4. Voicemail Hacking:
Voicemail systems utilizing VoIP networks may be exposed to various hacking techniques including brute-force attacks, exploitation of default passwords, and social engineering. Intruders are able to bypass the security for voicemail accounts to listen to messages, change the voicemail settings, or perform other malicious acts.
Example: Voicemail Hacking
Abuse is committed by an unauthorized person who breaks into a VoIP’s voicemail box nexium and brings out vital information.
For instance, the criminal in this case listens to voicemails that have been left for other employees and in the process gathers sensitive information that includes log-in details, sensitive financial information and important business strategies and plans.
For example, they could use the credentials obtained in $money laundering in initiating legal actions through fraudulencies and also selling introduced packed information into the dark web.
This assault gives us an idea how important it is to secure veils bore systems and also train the workers in the company on the risks associated with cyber security.
5. Toll Fraud:
With the help of such attacks, VoIP systems are intended for making calls even without an authorization, typically to expensive numbers and abroad causing money loss to many companies. This may consist of scenarios where user accounts are compromised, where there are poor configurations, and where VoIP trunks are taken over to make fake calls.
Toll fraud results in an astonishing loss of $27 billion, as reported by Trend Micro.
Example: Toll Fraud
For example, A small business’s Voice over Internet Protocol system has been compromised by hackers which lets criminals make illegal international or premium rate calls. The business owner only realizes the crime after the bill shock erupts when a sky high telephone bill contains charges that cannot be reconciled with calls made.
This type of fraud highlights the attention that has to be paid towards the system security and even attending to the system on a timely routine basis.
6. Phishing Attacks:
There are other missions attacking VOIP such as phishing. Phishing technique seeks the exploitation of users over VoIP systems to obtain confidential information such as logins and banking details. In such situations, scam VoIP calls could prevailing wherein the attacker uses a trusted third party to abuse users for information or malware installation.
Example: Phishing Attack
For example, the cybercriminals create phony emails which appear to belong to that company which is the voice over internet protocol provider and instructs employees to log on to remedy that problem. Employees fall into this trap and provide their details which are used by hackers to invade the VoIP system.
This empowers them with the skills to intercept conversations with other people over the extension or better yet, place illegal calls while logged onto the company’s account.
7. Man-in-the-Middle (MitM) Attacks:
Through MitM attacks, an individual identifies himself metaphorically, becomes part of the communication and constitutes himself as an enemy.
Often people look to Voice over Internet Protocol (Ignores), where they may be put in charge of a network server-inserting themselves in between two communicating persons and, therefore, hear, change, or add bad things into the conversation flow.
Example: MitM attack
One could visualize a situation where a bank statement is delivered to you only that it has been annotated by a person that never was intending to send it to you anyway.
A Man- in –the- Middle attack is like where a courier takes the statement of an account at the bank before it’s delivered to the post. The envelope is opened by a courier with hidden intentions
8. VoIP Protocol Exploitation:
Attackers are able to take advantage of certain vulnerabilities in VoIP protocols such as SIP and/or H.323 to obtain direct access which leads to arbitrary code execution and denial of service.
They may also find that they have irregularities in the fundamental structural design of the protocol which could permit attacks like the spam, where bad data could be inserted into a legitimate message or damaging attempts to attack virtual users by illicit displaying video replacement through normal video call protocols/policies.
Example: VoIP Protocol Exploitation
One possible case of such exploitation would be with the Session Initiation Protocol, SIP, a standard that connects IP-based calls with other IP services.
That’s not all, as they could also launch a simple denial-of-service attack, block calls, eavesdrop, or misroute calls. Updates and replacement must be made to cope with the odds of exposed attacks.
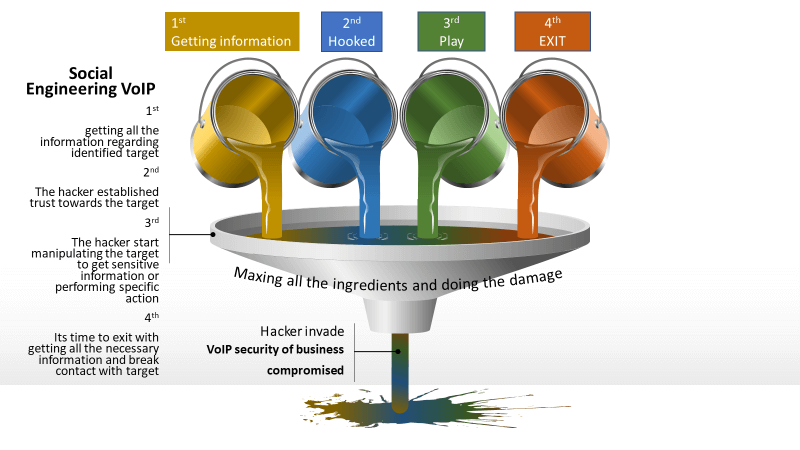
9. Social Engineering:
VoIP social engineering is characterized as the use of fraudulently obtained information in order to explain manipulation and interaction with people over internet based Voice protocol.
In general arena, hacking comprises only the technical aspects and leaves little room for contact with the people for traditional methods to listen and obtain information.
Example: Social Engineering
Proactive approaches to enhance VoIP security
Proactive approaches to enhance VoIP security” refers to pre-emptive measures taken to strengthen the security of Voice over Internet Protocol systems before potential threats or vulnerabilities can be exploited. Instead of merely reacting to security incidents after they occur, proactive approaches involve implementing preventive measures to mitigate risks and safeguard VoIP communications.
Perform periodic risk analysis and VoIP security audit in scanning for vulnerabilities and other weaknesses present in the VoIP infrastructure.

Proactive Voice over Internet Protocol Security measures may include:
| VoIP Security Measure | Explanation |
|---|---|
| Using Strong Encryption Protocols | For instance, Secure Real-time Transport Protocol (SRTP) encrypts voice packets to prevent eavesdropping. If an attacker intercepts VoIP traffic without encryption, they might listen in on conversations, including sensitive information like bank accounts, passwords, or social security numbers. |
| Implementing Access Control Measures | Requiring users to identify themselves with a username and password before using VoIP services can deter unauthorized individuals from making calls or accessing sensitive information. Without these measures, attackers could gain access, eavesdrop, or launch attacks. |
| Deploying Intrusion Detection and Prevention Systems (IDS/IPS) | IDS/IPS systems detect and block SIP flooding or brute-force attacks, ensuring VoIP systems are protected. Without these systems, VoIP could be vulnerable to attackers exploiting vulnerabilities. |
| Educating Users about VoIP Security Threats | Phishing awareness training helps users identify scams like phishing emails or vishing. Without this training, users are more susceptible to social engineering attacks that can compromise VoIP systems and steal sensitive data. |
| Keeping VoIP Software, Firmware, and Devices Updated | Proper firewall configuration blocking unauthorized VoIP protocols or IP addresses can prevent attacks like DoS. Without this, VoIP systems could be exposed to SIP scanning or toll fraud. |
| Monitoring VoIP Systems and Networks for Anomalies | Logging VoIP call details and analyzing records helps detect anomalies, such as unauthorized access attempts. Without proper monitoring, attacks may go unnoticed, leaving systems vulnerable. |
| Implementing Network Segmentation | Segmenting voice traffic into a separate VLAN ensures voice packets are isolated from data, reducing the risk of attacks. Without segmentation, an attack on one part of the network could compromise VoIP communications. |
Final Verdict
With the rise of Voice over Internet Protocol, a need emerges for its protection from attacks. Strong encryption, reliable service providers, up-to-date software and network security policies to maintain the integrity of the Voice over Internet Protocol system can help prevent intrusions into the system.
Especially, raising users’ awareness of the risks involved and communication methods that are secure is necessary. It is with such measures that VoIP can be effective and private calls can be maintained as expected.
FAQs: VoIP hacking
Yes, VoIP can be secure if proper security measures are in place. Implementing encryption, strong passwords, regular updates, and network security protocols can help mitigate risks associated with VoIP, making it a secure communication option.
VoIP systems can be hacked. Weak spots in how they work can let hackers get in. To keep them safe, you need strong security measures like encryption and passwords.
VoIP hacking involves unauthorized access or manipulation of Voice over Internet Protocol (VoIP) systems. It encompasses various methods attackers use to intercept calls, eavesdrop on conversations, make unauthorized calls, or disrupt communication services.
Hackers gain access to VoIP systems by exploiting weak passwords, executing phishing attacks to obtain login credentials, exploiting software vulnerabilities, or manipulating individuals within an organization through social engineering tactics.
The risks associated with VoIP hacking include unauthorized access to sensitive information, toll fraud resulting in financial losses, service disruption through denial-of-service attacks, and damage to the organization's reputation and credibility.
To protect your VoIP system, consider implementing measures such as using strong, unique passwords, enabling encryption protocols like Secure Real-time Transport Protocol (SRTP), regularly updating software to patch vulnerabilities, deploying network security measures like firewalls and intrusion detection systems, and educating users on security best practices.
If you suspect your VoIP system has been hacked, change all passwords associated with compromised accounts immediately, notify your VoIP service provider and IT security team, review call and network traffic logs, implement additional security measures like multi-factor authentication, and consider consulting with a cybersecurity expert for a thorough security assessment.